What Hashing Algorithm Does Bitcoin Use to Hash Blocks?
So, what really is hashing?
TLDR:
- Hashing is generating a value or values from a string of text using a mathematical function.
- Hashing is 1 fashion to enable security during the process of message manual when the message is intended for a particular recipient only. A formula generates the hash, which helps to protect the security of the transmission confronting tampering.
It is important to know how blockchain Hashing works. In order to practise that, however, we need to first empathize one of the core principles that go into blockchain creation. Blockchain applied science is 1 of the virtually innovative and era-defining discoveries of the past century. Seeing the influence it has had over the last few years and the bear upon that it will have in the hereafter, information technology surely isn't an exaggeration to say that. In gild to understand how various cryptocurrencies like Ethereum and Bitcoin function.
And then what is hashing?
In simple terms, hashing means taking an input string of whatever length and giving out an output of a fixed length . In the context of cryptocurrencies similar bitcoin, the transactions are taken as input and run through a hashing algorithm ( bitcoin uses SHA-256) which gives an output of a stock-still length.
Allow's come across how the hashing process works. Nosotros are going put in certain inputs. For this practice, we are going to use the SHA-256 (Secure Hashing Algorithm 256).
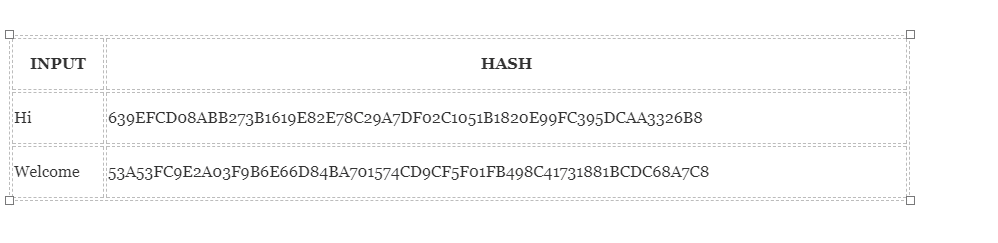
As you can meet, in the instance of SHA-256 , no thing how big or pocket-size your input is, the output will ever have a fixed 256-bits length. This becomes critical when you lot are dealing with a huge corporeality of data and transactions. So basically, instead of remembering the input data which could be huge, you tin simply remember the hash and keep runway. Before we become whatever farther we need to offset see the various backdrop of hashing functions and how they get implemented in the blockchain.
Cryptographic hash functions
A cryptographic hash office is a special class of hash functions that has various properties making it platonic for cryptography. There are certain backdrop that a cryptographic hash part needs to have in guild to exist considered secure. Let'due south run through them i by ane.
Property 1: Deterministic
This means that no matter how many times you parse through a particular input through a hash function you lot volition always get the same consequence. This is critical because if yous get unlike hashes every single fourth dimension information technology will be impossible to keep rail of the input.
Belongings 2: Quick Computation
The hash function should be capable of returning the hash of input quickly. If the procedure isn't fast enough and so the arrangement simply won't be efficient.
Holding three: Pre-Image Resistance
What pre-epitome resistance states are that given H(A) it is infeasible to determine A, where A is the input and H(A) is the output hash. Notice the apply of the word "infeasible" instead of "impossible". Nosotros already know that it is not impossible to determine the original input from its hash value. Allow's take an example.
Suppose you lot are rolling a dice and the output is the hash of the number that comes up from the dice. How will you be able to decide what the original number was? Information technology's simple all that y'all have to practise is to detect out the hashes of all numbers from 1-6 and compare. Since hash functions are deterministic, the hash of a particular input will always exist the same, and then you tin but compare the hashes and find out the original input.
But this only works when the given amount of data is very less. What happens when yous have a huge corporeality of data? Suppose you are dealing with a 128-bit hash. The only method that you lot have to detect the original input is by using the "animate being-force method". The brute-force method basically ways that you have to option up a random input, hash information technology and so compare the output with the target hash and echo until y'all find a lucifer.
So, what will happen if y'all use this method?
- Best instance scenario: You go your answer on the first endeavour itself. Y'all volition seriously accept to exist the luckiest person in the world for this to happen. The odds of this happening are astronomical.
- Worst example scenario: Y'all get your answer after 2^128 – 1 times. Basically, it ways that you volition find your answer at the end of all the data.
- Boilerplate scenario: You volition detect it somewhere in the middle so basically after ii^128/2 = ii^127 times. To put that into perspective, 2^127 = 1.7 X 10^38. In other words, it is a huge number.
So, while information technology is possible to suspension pre-paradigm resistance via the beast force method, it takes so long that it doesn't matter.
Property 4: Small Changes In The Input Changes the Hash.
Even if y'all make a small change in your input, the changes that will exist reflected in the hash will be huge. Let's test it out using SHA-256:
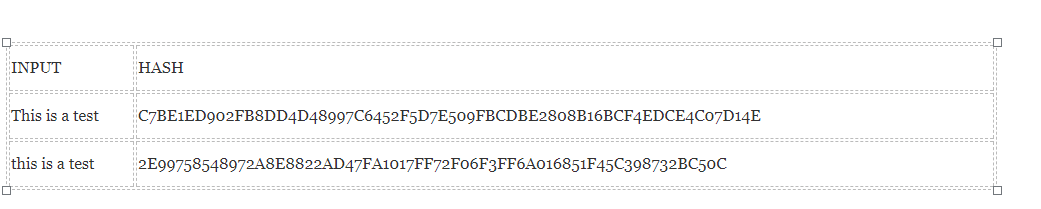
Exercise you see that? Fifty-fifty though you just changed the example of the first alphabet of the input, look at how much that has affected the output hash. This is a critical role because this property of hashing leads to one of the greatest qualities of the blockchain, its immutability (more on that afterward.)
Belongings 5: Collision Resistant
Given 2 dissimilar inputs A and B where H(A) and H(B) are their respective hashes, it is infeasible for H(A) to be equal to H(B). What that means is that for the about office, each input will have its own unique hash. Why did nosotros say "for the most part"? Let's talk about an interesting concept called "The Birthday Paradox".
What is the Birthday Paradox?
If you meet any random stranger out on the streets the chances are very low for both of yous to have the aforementioned birthday. In fact, assuming that all days of the year have the same likelihood of having a birthday, the chances of another person sharing your altogether is i/365 which is 0.27%. In other words, it is actually low.
Even so, having said that, if you gather up 20-xxx people in one room, the odds of two people sharing the exact aforementioned altogether rises up astronomically. In fact, there is a 50-50 adventure for 2 people sharing the same birthday in this scenario!
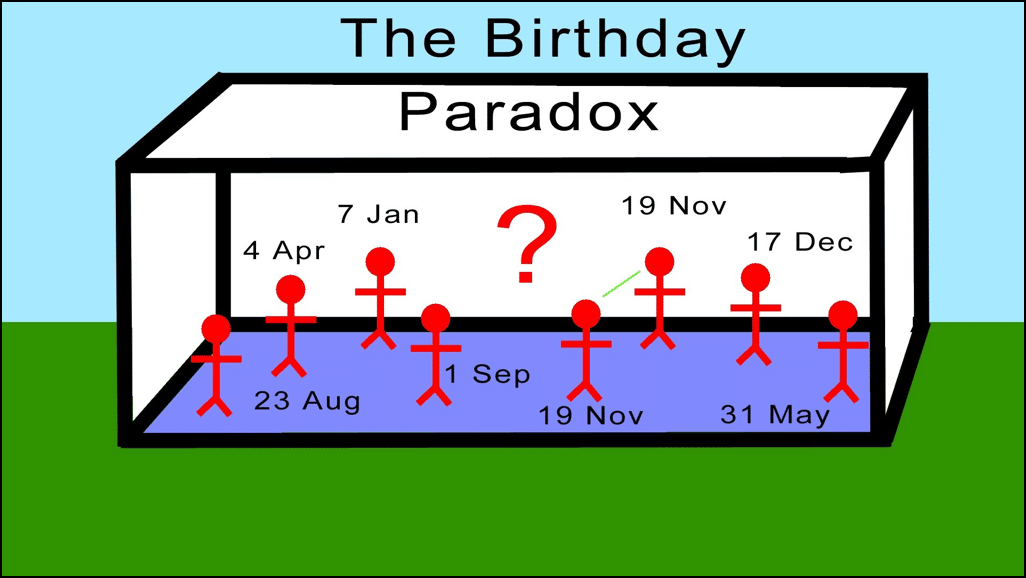
Image credit: (YouTube)
Why does that happen? Information technology is considering of a simple rule in probability which goes as follows. Suppose you have Due north dissimilar possibilities of an outcome happening, and so y'all need square root of N random items for them to accept a l% chance of a collision.
So applying this theory for birthdays, yous have 365 different possibilities of birthdays, so you but need Sqrt(365), which is ~23~, randomly chosen people for fifty% adventure of two people sharing birthdays.
What is the awarding of this in hashing?
Suppose you have a 128-flake hash which has 2^128 different possibilities. Past using the birthday paradox, you take a 50% chance to intermission the standoff resistance at the sqrt(2^128) = 2^64th instance.
As you tin can see, it is much easier to break collision resistance than information technology is to break preimage resistance. No hash function is collision free, just it normally takes and so long to detect a collision. So, if you are using a function like SHA-256, information technology is safe to assume that if H(A) = H(B) then A = B.
Property six: Puzzle Friendly
Now, this is a fascinating property, and the application and impact that this one property has had on cryptocurrency are huge (more on that later when we cover mining and crypto puzzles). First let's define the holding, later on that we volition go over each term in detail.
For every output "Y", if k is chosen from a distribution with high min-entropy it is infeasible to find an input x such that H(k|10) = Y.
That probably went all over your caput! Merely information technology's ok, let's at present understand what that definition means.
What is the meaning of "high min-entropy"?
It ways that the distribution from which the value is chosen is hugely distributed and then much so that united states of america choosing a random value has a negligible probability. Basically, if y'all were told to chose a number betwixt 1 and 5, that'south a low min-entropy distribution. However, if you were to cull a number between 1 and a gazillion, that is a high min-entropy distribution.
What does "chiliad|10" mean?
The "|" denotes concatenation. Concatenation means adding two strings together. Eg. If I were to concatenate "BLUE" and "Heaven" together, and then the result volition be "BLUESKY".
So now let's revisit the definition.
Suppose y'all accept an output value "Y". If you choose a random value "k" from a broad distribution, it is infeasible to find a value 10 such that the hash of the concatenation of k and ten will give the output Y.
Once over again, notice the give-and-take "infeasible", it is not incommunicable because people exercise this all the time. In fact, the whole process of mining works upon this (more on that afterward).
Examples of cryptographic hash functions
- Medico 5: It produces a 128-bit hash. Collision resistance was broken after ~2^21 hashes.
- SHA 1: Produces a 160-bit hash. Collision resistance bankrupt later ~2^61 hashes.
- SHA 256: Produces a 256-bit hash. This is currently being used by bitcoin.
- Keccak-256: Produces a 256-fleck hash and is currently used past ethereum.
Hashing and data structures
A information structure is a specialized way of storing data. At that place are 2 information structure properties that are disquisitional if yous want to understand how a blockchain works. They are:
- Pointers.
- Linked Lists.
Pointers
Pointers are variables in programming which stores the address of another variable. Usually normal variables in any programming language store information.
Eg. int a = x, means that there is a variable "a" which stores integer values. In this instance, it is storing an integer value which is 10. This is a normal variable.
Pointers, however, instead of storing values will shop addresses of other variables. Which is why they are called pointers, because they are literally pointing towards the location of other variables.
Linked Lists
A linked listing is one of the most important items in data structures. This is what a linked list looks like:
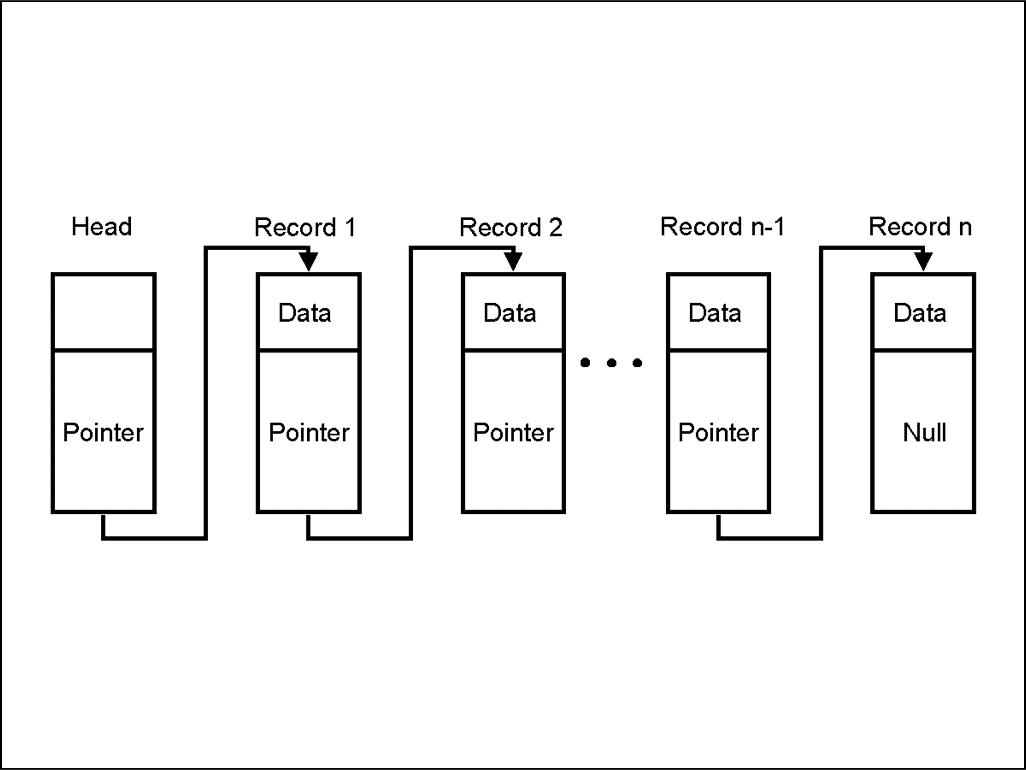
It is a sequence of blocks, each containing data that is linked to the next block via a pointer. The pointer variable, in this case, contains the accost of the next node in it and hence the connection is made. The last node, as y'all can see, has a cypher pointer which means that information technology has no value.
I of import thing to note here, the pointer inside each block contains the accost of the next block. That is how the pointing is achieved. Now you might be request what does that means for the first block in the listing? Where does the pointer of the first cake stay?
The first block is called the "genesis cake" and its pointer lies out in the organization itself. It sort of looks like this:
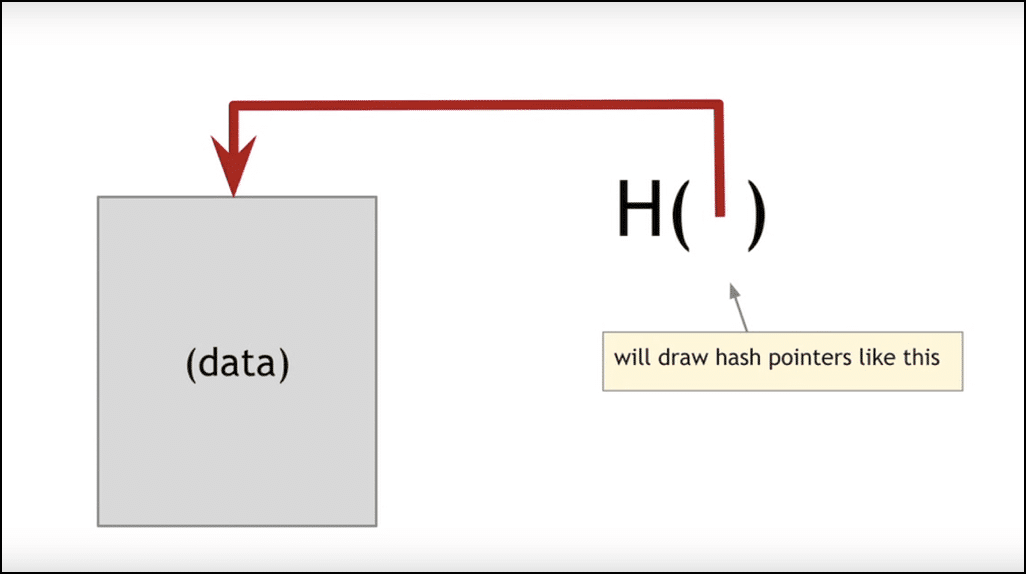
Image courtesy: Coursera
If you are wondering what the "hash arrow" means, we will get there in a bit.
Every bit you may accept guessed past now, this is what the structure of the blockchain is based on. A blockchain is basically a linked list. Allow's see what the blockchain structure looks like:
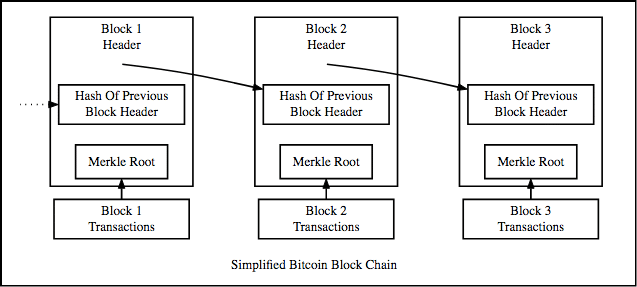
The blockchain is a linked list that contains data and a hash pointer that points to its previous block, hence creating the chain. What is a hash arrow? A hash arrow is similar to a arrow, simply instead of simply containing the accost of the previous block it also contains the hash of the information within the previous block. This one modest tweak is what makes blockchains so amazingly reliable and trailblazing.
Imagine this for a 2nd, a hacker attacks cake 3 and tries to change the information. Because of the properties of hash functions, a slight modify in data volition change the hash drastically. This ways that any slight changes fabricated in block three, volition change the hash which is stored in block 2, now that in turn will change the information and the hash of block ii which will result in changes in block 1 and and so on and so along. This volition completely change the chain, which is impossible. This is exactly how blockchains attain immutability.
So what does a block header look similar?
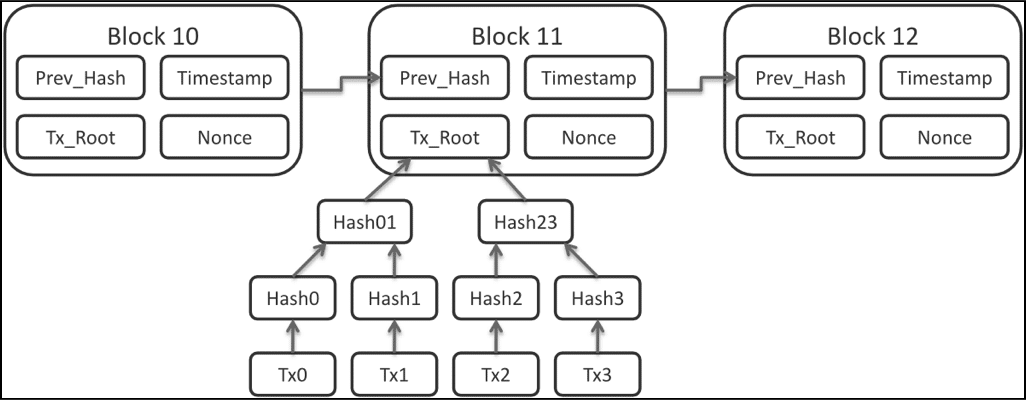
A block header contains:
- Version: The cake version number.
- Time: the current timestamp.
- The current difficulty target. (More on this later).
- Hash of the previous block.
- Nonce (more on this afterward).
- Hash of the Merkle Root.
Right at present, allow's focus on the Hash of the Merkle Root. Just earlier that, nosotros need to understand what a Merkle Tree is.
What is a Merkle Tree?
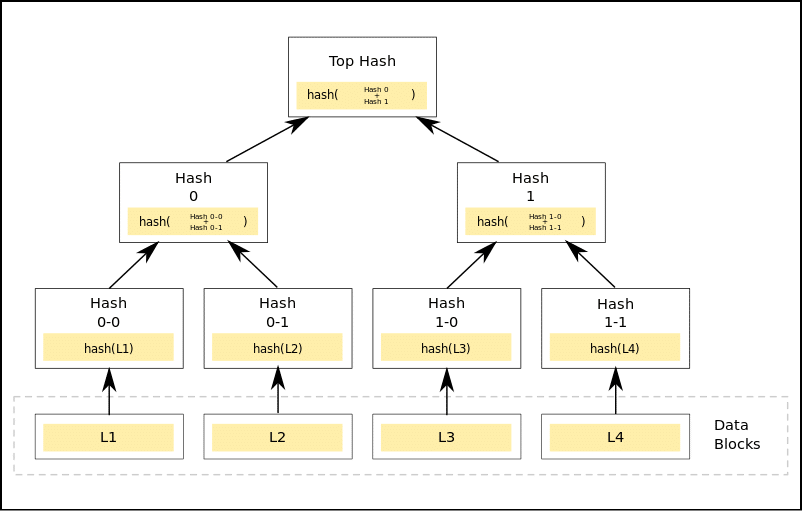
Image Courtesy: Wikipedia
The in a higher place diagram shows what a Merkle tree looks like. In a Merkle tree, each non-leafage node is the hash of the values of their child nodes.
Leaf Node: The leaf nodes are the nodes in the everyman tier of the tree. Then wrt the diagram above, the leafage nodes will be L1, L2, L3 and L4.
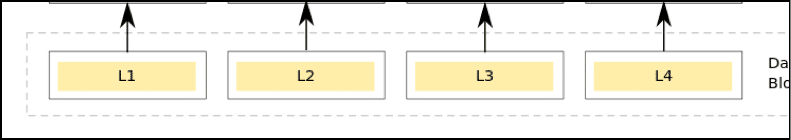
Child Nodes: For a node, the nodes below its tier which are feeding into information technology are its kid nodes. Wrt the diagram, the nodes labeled "Hash 0-0" and "Hash 0-1" are the child nodes of the node labeled "Hash 0".
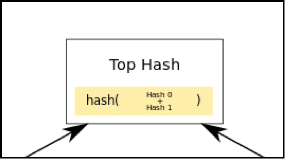
Root Node: The single node on the highest tier labeled "Top Hash" is the root node.
And so what does a Merkle Tree have to practise with blockchains?
Each block contains thousands and thousands of transactions. It will be very fourth dimension inefficient to store all the information inside each block as a serial. Doing so will make finding whatever item transaction extremely cumbersome and fourth dimension-consuming. If y'all utilise a Merkle tree, however, yous will greatly cut downward the time required to discover out whether a detail transaction belongs in that cake or not.
Allow's see this in an instance. Consider the following Merkle tree:
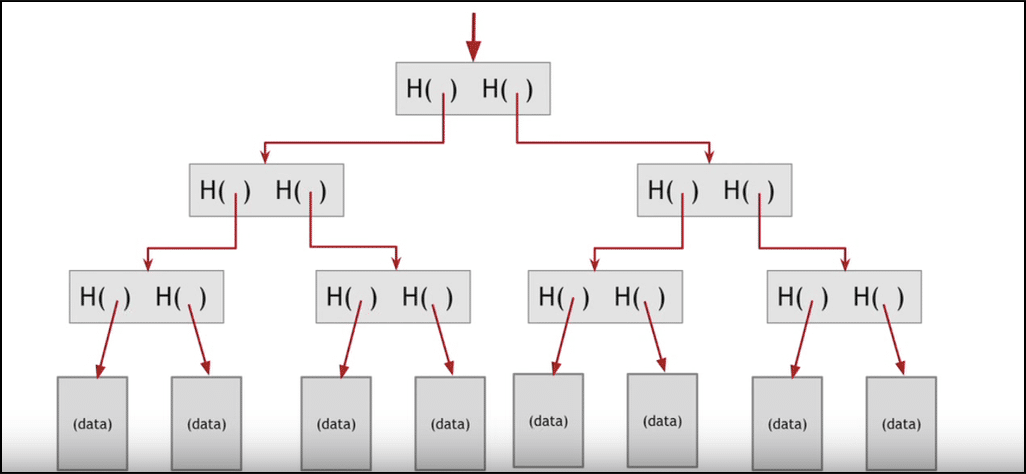
Epitome courtesy: Coursera
Now suppose I want to find out whether this detail data belongs in the block or non:
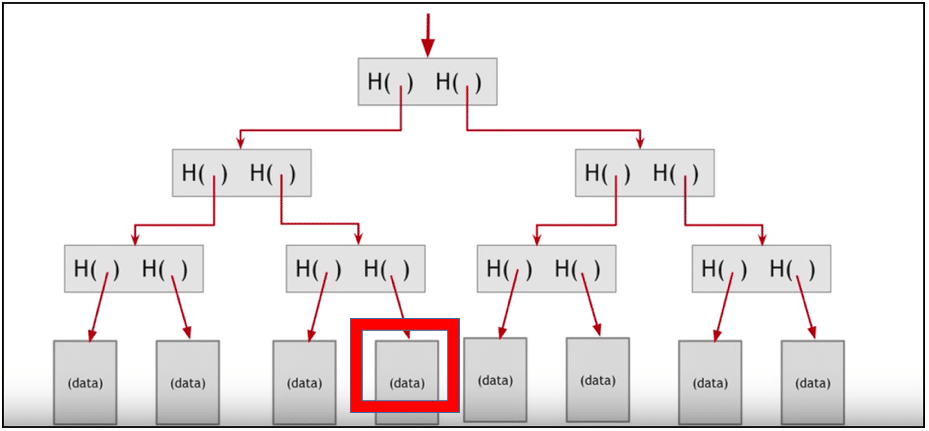
Instead of going through the cumbersome process of looking at each individual hash and seeing whether it belongs to the data or not, I can simply runway it downwards past following the trail of hashes leading up to the data:
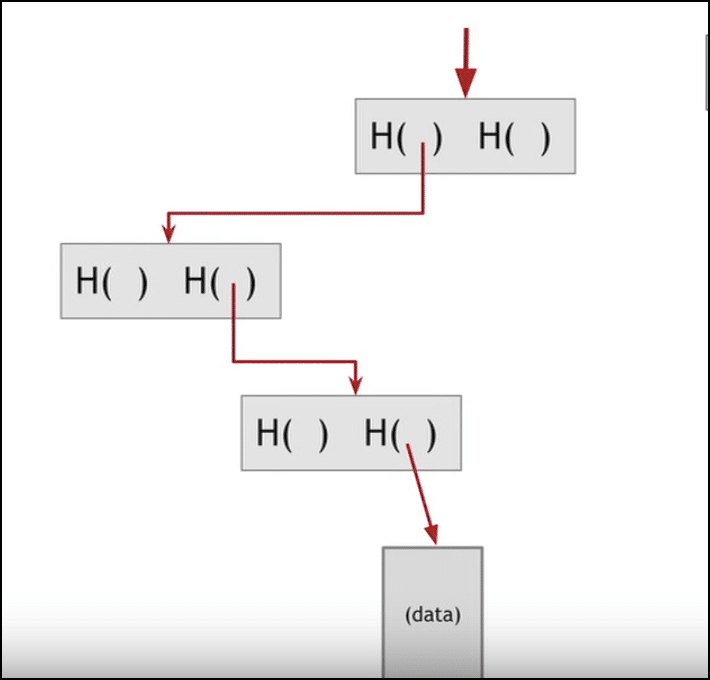
Doing this significantly reduces the time taken.
Hashing in mining: The crypto puzzles.
When we say "mining", information technology basically means searching for a new block to be added in the blockchain. Miners from around the world are constantly working to brand sure that the chain keeps on growing. Before information technology used to exist easy for people to mine using merely their laptops, but over fourth dimension, people started forming mining pools to pool in their computer powers and mine more than efficiently.
This, yet, could have been a problem. There is a cap for each cryptocurrency, eg. for bitcoin, information technology is just 21 1000000. There are only 21 million bitcoins out there. If the miners are allowed to carry on, at this rate, they will fish out all the bitcoins in beingness. On top of that, there needs to be a specific fourth dimension limit in between the creation of each blocks. For bitcoin, the fourth dimension limit in between block creation is 10 mins. If the blocks were allowed to be created faster, it would event in:
- More than collisions: More hash functions will be generated which volition inevitably cause more collisions.
- More than orphaned blocks: If a lot of miners are over mining they will come up with new blocks simultaneously. This will result in or more blocks non getting to be part of the main chain and becoming orphan blocks.
So, in order to restrict block creation, a specific difficulty level is fix. Mining is like a game, you solve the puzzle and you get rewards. Setting difficulty makes that puzzle much harder to solve and hence more than time-consuming. WRT bitcoins the difficulty target is a 64-character string (which is the same as a SHA-256 output) which begins with a agglomeration of zeroes. A number of zeroes increases as the difficulty level increases. The difficulty level changes after every 2016th cake.
The mining procedure
Note: We will primarily be talking about Bitcoin mining hither.
When the bitcoin mining software wants to add a new block to the blockchain, this is the procedure information technology follows. Whenever a new block arrives, all the contents of the blocks are kickoff hashed. If the hash is lesser than the difficulty target, then it is added to the blockchain and everyone in the community acknowledges the new cake.
However, it is not as simple equally that. You will accept to be extremely lucky to get a new block simply like that. This is where the nonce comes in. The nonce is an arbitrary cord that is concatenated with the hash of the block. After that this concatenated string is hashed over again and compared to the difficulty level. If it is not less than the difficulty level, then the nonce is inverse and this keeps on repeating a million times until finally, the requirements are met. When that happens the cake is added to the blockchain.
And so to recap:
- The hash of the contents of the new block is taken.
- A nonce (random string) is appended to the hash.
- The new string is hashed once more.
- The final hash is so compared to the difficulty level and seen whether it'south actually less than that or not.
- If not, then the nonce is inverse and the process repeats again.
- If aye, and so the block is added to the concatenation and the public ledger is updated and alerted of the addition.
- The miners responsible for this are rewarded with bitcoins.
Remember property number half dozen of hash functions? The puzzle friendliness?
For every output "Y", if chiliad is chosen from a distribution with high min-entropy it is infeasible to find an input x such that H(thou|10) = Y.
Then, when it comes to bitcoin mining:
- 1000 = Nonce
- ten= the hash of the cake
- Y = the difficulty target
The entire process is completely random, there is no thought process behind the selection of the nonces. It is just pure brute-force where the software keeps on randomly generating strings till they accomplish their goal. The entire process follows the Proof Of Work protocol which basically means:
- The puzzle-solving should be hard.
- Checking the answer should, all the same, be piece of cake for anybody. This is done to make sure that no underhanded methods were used to solve the problem.
What is hash rate?
Hash rate basically means how fast these hashing operations are taking identify while mining. A high hash rate means more people and software machines are taking part in the mining procedure and as a result, the organization is running smoothly. If the hash rate is too fast the difficulty level is increased. If the hash rate becomes besides deadening then the difficulty level is decreased.
Decision- What Is Hashing?
Hashing has truly been fundamental in the creation of blockchain engineering. If i wants to sympathize what the blockchain is all about, they should definitely empathize what hashing means.
Source: https://blockgeeks.com/guides/what-is-hashing/
0 Response to "What Hashing Algorithm Does Bitcoin Use to Hash Blocks?"
Post a Comment